The Digital Tattoo that protects your sensitive and confidential documents

Secure

Adaptive

Cost-effective
Thanks to our advanced technology, the rapid detection of potential breaches enables early intervention to minimize losses, resulting in effective risk management and reduced costs associated with potential data leaks.

Imperceptible
The discretion of our digital tattoo solution ensures that users will not be aware of its presence, thereby preserving the integrity and confidentiality of shared documents.

Versatile
Our watermarking has been designed to seamlessly integrate into existing workflow processes without disrupting the usual functionalities of files, allowing for a smooth and unhindered user experience.

Resilient
Despite attempts at manipulation such as printing, scanning, or even taking screenshots, the digital tattoo remains intact, preserving the traceability and authenticity of the documents involved, even in the face of malicious acts, especially when handled outside the secure and collaborative Wimi suite.
The technology of “Digital Tattoo”
Cutting-edge watermarking for unparalleled protection and flawless traceability.
Watermarking, as a principle, involves the subtle incorporation or concealment of a message within a host medium such as an image, a database, or a document, with the aim of securing this medium in terms of copyright, integrity, or traceability. For example, it allows for the concealment of user or buyer identifiers within the host medium. The host medium remains accessible while being protected by the hidden message. This protection is independent of the data storage format and does not alter the usual functionalities, as the message remains imperceptible. This adaptability gives watermarking considerable relevance in securing sensitive data.
In comparison to its competitors in the field of watermarking, Wimi Tattoo offers a solution for document and data protection and traceability based on reversible watermarking. This reversible property ensures the possibility of removing the watermark from the concerned document, thus allowing for the precise recovery of the original host medium.
En pratique, comment fonctionne le Tatouage Numérique Wimi Tatoo ?
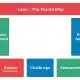
Creation
Editing of original data/documents within the sovereign and secure collaborative suite Wimi.
Marking
From the Wimi suite, activation on demand to facilitate sharing or automatically after a download.
Share
Transmission of data to a partner or extraction by a collaborator.
Leak
Total or partial disclosure of shared information.
Identification
Data retrieval online, tag extraction, and origin identification.
Data leaks have significant consequences.
Internal data leaks: a major financial and organizational challenge for French companies.
A significant proportion, approximately 60%, of data leakage incidents are related to authorized internal users, including employees, partners, or subcontractors, who disclose sensitive company information. These internal leaks have major repercussions, often resulting in significant financial losses estimated at several million euros, as well as considerable damage to the organizational structure, heavily impacting overall business operations. Indeed, the investigation conducted by the Ponemon Institute on behalf of IBM in 2019 revealed that the average cost of data breach incidents amounts to 3.65 million euros in France.
What are the origins of internal data leaks?
Share
During your daily operations, you exchange data with your collaborators, partners, and subcontractors, which can constitute a potential source of leaks.
Negligence
Handling errors, loss of storage media such as USB drives, or even accessing suspicious websites via phishing attacks can all lead to data leakage incidents.
Malicious intent
Loss
The inadvertent exposure or hacking of your sensitive data on the internet can make it accessible to hackers and competitors.
Share
During your daily operations, you exchange data with your collaborators, partners, and subcontractors, which can constitute a potential source of leaks.
Negligence
Handling errors, loss of storage media such as USB drives, or even accessing suspicious websites via phishing attacks can all lead to data leakage incidents.
Malicious intent
Unauthorized transfer of data or copying of sensitive information before the departure of an employee/manager are common malicious behaviors leading to data leaks.
Loss
The inadvertent exposure or hacking of your sensitive data on the internet can make it accessible to hackers and competitors.
Questions/Answers about Digital Tattoo
Quickly find an answer to your question
How to identify and what are the sensitive and confidential documents to protect in the company with a digital tattoo?
To identify sensitive and confidential documents within the company, it is crucial to consider various aspects. Generally, a document is considered confidential if it contains personal data such as names, addresses, social security numbers, email addresses, phone numbers, or if it contains strategic information. Furthermore, the confidential nature of a document can be defined by the laws and regulations governing data management in the professional field. These regulations impose on organizations the legal obligation to protect the data of their customers and employees by respecting confidentiality, which includes setting archiving deadlines and destroying archives.In this perspective, among the sensitive and confidential documents of the company, we can mention financial documents such as credit and debit account statements, credit applications, as well as information on financial and real estate transactions. Documents related to the organization's business strategy, such as profit and loss accounts, trade secrets, documents relating to intellectual property, and tax information, also require special protection. Similarly, invoices, confidential correspondence, contact information, shipping labels, as well as various documents concerning management, research and development, human resources, accounting, sales and marketing, as well as information on suppliers and partners, should be considered sensitive and protected accordingly.
What is the difference between reversible and non-reversible tattooing?
A reversible tattoo allows specific information to be added and removed from a digital medium without affecting its quality or integrity. In contrast, a non-reversible tattoo is permanently embedded in the medium and cannot be removed without altering the medium itself.
What are the advantages of digital tattooing compared to other data protection methods?
Unlike some data protection techniques that can be circumvented or removed, digital tattooing offers discreet and integrated protection that generally remains intact even after manipulation or attempted falsification.
Does digital tattooing contribute to compliance with data security standards?
By ensuring the traceability and integrity of sensitive information, digital tattooing helps companies comply with data security standards by providing a reliable method to protect sensitive data from unauthorized leaks and manipulations.
Can digital tattooing track the spread of sensitive data?
Digital tattooing creates unique fingerprints that allow tracking the trajectory of sensitive data, facilitating the detection of any unauthorized use or disclosure, even after their initial sharing.
How can digital tattooing be used to prevent counterfeiting or falsification of documents?
By incorporating specific marks into documents, digital tattooing makes counterfeiting or falsification difficult, as any alteration of the content can be easily detected through the embedded unique digital fingerprints.
How can digital tattooing be used to prove the authenticity of documents in legal disputes?
The unique digital fingerprints created by digital tattooing can serve as strong evidence to verify the authenticity of documents in legal disputes, thus enhancing the credibility of the information contained in these documents.
Does digital tattooing affect the quality of the media?
Digital tattooing is designed to be imperceptible and generally does not affect the visual quality or readability of the host medium. This approach ensures that end users can access the content without encountering unwanted disruptions due to tattooing.